3DES vs AES: Which Algorithm Should You Use?
While the mathematical specifics of digital encryption are complicated, the importance is easy to understand. In a world where digital security is the backbone of both personal and professional lives, understanding and selecting the right encryption algorithm is crucial.
Two of the most popular and well-entrenched options for digital encryption and decryption are 3DES (Triple Data Encryption Standard) and AES (Advanced Encryption Standard). In this blog, we'll dive into the specifics of each, discuss their differences, explore their real-world applications, and ultimately produce a verdict regarding which option might be the right choice for your needs. We'll also discuss how CData Arc can leverage both of these encryption standards to create secure Managed File Transfer, EDI, and data integration workflows.
What is 3DES?
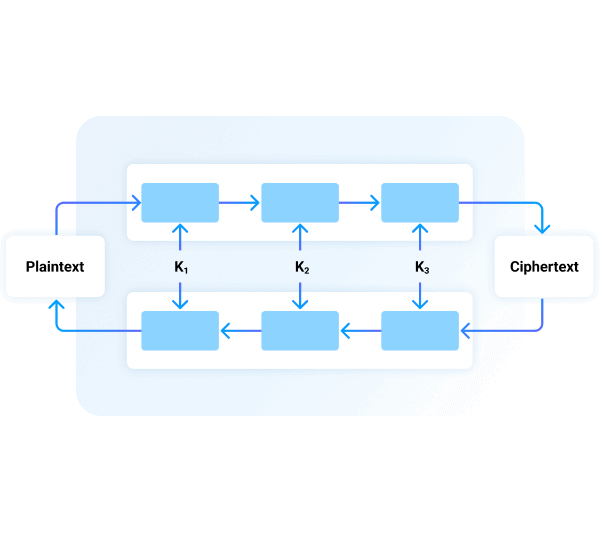
3DES, also known as Triple DES, is the evolution of an encryption algorithm called DES (Data Encryption Standard) which was developed by IBM in the early 1970s. 3DES relies on the same mathematical and cryptographical concepts as DES, but – as the name implies – performs three separate encryption operations with three separate encryption keys.
By increasing the number of keys and operations, 3DES provides significantly higher security than its predecessor. 3DES outperformed DES in regards to resisting brute force attacks – a common type of hacking attempt that is conceptually the same as trying every possible number combination on a keypad.
3DES quickly overtook DES as the encryption algorithm of choice, but its integral relationship with a cryptographic standard from the 70s proved problematic. As digital security and counter-security advanced at their typical break-neck pace, conceptual weaknesses in the original DES scheme threatened 3DES in turn.
3DES is not truly “broken,” since there are no feasible ways to deterministically crack the cipher, but it remains vulnerable to a type of probabilistic attack known as Sweet32 – a type of Birthday Attack that depends on randomly occurring coincidences like meeting someone with the same birthday as yours.
What is AES?
AES, or Advanced Encryption Standard, was established by the U.S. National Institute of Standards and Technology (NIST) in 2001 to replace DES and 3DES as the go-to encryption standard. Like 3DES, AES is a symmetric key encryption algorithm that uses the same encryption key for both encrypting and decrypting data. Having learned the same lesson from DES that spurred the development of 3DES, AES encryption keys are large enough to effectively prohibit brute force attacks.
To solve probabilistic vulnerabilities like those leveraged by Sweet32, AES operates on larger blocks of text at a time – this decreases the likelihood of the type of coincidences upon which Birthday Attacks depend. While the mathematical details of AES extend far beyond the scope of this blog, it suffices to say that the operations within AES encryption are significantly more complex than prior encryption methods: Substitutions, permutations, mixing of plaintext and cipher, repetition, and large input sizes.
How are 3DES and AES different?
The primary differences between 3DES and AES lie in their structure, speed, security level, and key lengths:
- Structure: While 3DES applies the DES algorithm three times per data block, AES uses a more complex set of operations (substitution, permutation, and mixing) applied over multiple rounds.
- Speed: AES is generally faster than 3DES, especially in hardware implementations. This speed advantage is due to AES's more efficient algorithmic structure and its ability to better utilize modern processor architectures.
- Key lengths: 3DES uses three 56-bit keys (effectively 112 bits), while AES supports key sizes of 128, 192, and 256 bits.
In perhaps more practical terms, 3DES is an older standard that performed well during its heyday but is simply outclassed by the more modern AES. While a significant amount of effort and sophistication is required to break 3DES ciphers, the process is conceptually understood and syndicated. AES provides security without any as-of-yet-discovered theoretical vulnerabilities.
The real-world applications of 3DES and AES
Both 3DES and AES are used to secure electronic data. When data is sent across the internet, it is relatively trivial for an attacker to gain access to the bytes of data in transfer. If the data is not encrypted, then such an attacker can simply read the data and effectively steal whatever the data contains.
If the data is encrypted, however, the bytes are not readable by themselves. Rather, the encryption key is required to first perform a cryptographic operation on the raw bytes to recover the plaintext version of the data. Thus, encryption algorithms ensure that, even if an attacker were to get their hands on your data, it would do them no good.
In real-world applications, the usage of 3DES and AES can differ based on industry requirements and security needs:
3DES: It has been prominently used in the banking sector, especially for ATM and PIN encryption. However, its use is declining due to slower processing speeds and emerging security concerns. It remains in use for legacy systems where upgrading to AES is not feasible.
AES: Due to its higher security and efficiency, AES is extensively used in various domains, including government communications, secure file transfers, SSL/TLS for internet security, and encrypting sensitive data in databases and applications. It's the standard for new systems and is recommended for any new encryption needs.
Which is more secure, 3DES or AES?
Without a doubt, AES is more secure than 3DES. Its larger key sizes and more sophisticated encryption processes provide a stronger defense against brute-force attacks and cryptographic analysis. The larger block size upon which AES performs cryptographic operations significantly reduces the chance of mathematical coincidences that give rise to Birthday Attacks. Thus, AES is resistant to the same types of attacks that 3DES resists and is invulnerable to attacks like Sweet32 that conceptually threaten 3DES.
While 3DES was a significant improvement over the original DES, it is considered vulnerable and outdated compared to AES, especially against modern cyber threats. The vulnerabilities of 3DES and its shorter key length have led to its deprecation by major standards organizations. In contrast, AES, with its robust security features, is not only currently considered secure against all known attack vectors but is also set to remain so for the foreseeable future.
How CData Arc creates secure MFT workflows
CData Arc provides secure managed file transfer (MFT) automation for organizations to exchange critical business data with their trading partners. While data security is always important, the scenarios that Arc is designed to handle are arguably some of the most security-dependent scenarios in the modern world.
Arc leverages AES as its default symmetric encryption standard to ensure that your data is not vulnerable, even conceptually, to modern cyberattacks. While AES is not always displayed prominently in the operations that Arc performs, it is used under-the-hood in many protocols that involve cryptography, like AS2 or FTPS.
In addition to AES, CData Arc supports a range of security features, including SSL/TLS, SSH File Transfer Protocol (SFTP), and comprehensive auditing capabilities. This ensures that all file transfers are secure, reliable, and interoperable. By choosing a platform like CData Arc that prioritizes high-level encryption standards, organizations can ensure the integrity and confidentiality of their data during transfer processes.
If you are interested in upgrading the security of your critical business data, you can begin building secure & reliable MFT automations immediately with a free trial of CData Arc.
Try CData Arc today
Start building secure MFT automations today with a 30-day free trial of CData Arc.





