Discover how a bimodal integration strategy can address the major data management challenges facing your organization today.
Get the Report →Hybrid & multi-cloud
CData Virtuality enables hybrid- and multi-cloud architectures
Benefit from the independence, flexibility, and scalability of enabling this modern architecture with CData Virtuality while ensuring transparency, governance and security.
- Customization: Benefit from the flexibility to hand-select and integrate the tools that work for your org, no matter where they are deployed.
- Scalability: Scale resources up or down based on demand to optimize performance and cost.
- Compliance & security: Meet regulatory requirements by storing sensitive data in a private cloud or on-prem, while leveraging public cloud services to improve workloads.
Versatile data management with CData Virtuality
CData Virtuality helps your team build and optimize the tech stack that works for you. Plug the gaps left by cloud platforms with versatile data management capabilities such as data integration, data quality, data governance, master data management, and metadata management so that you can build the architecture that you want, deployed where you want.
How CData Virtuality works
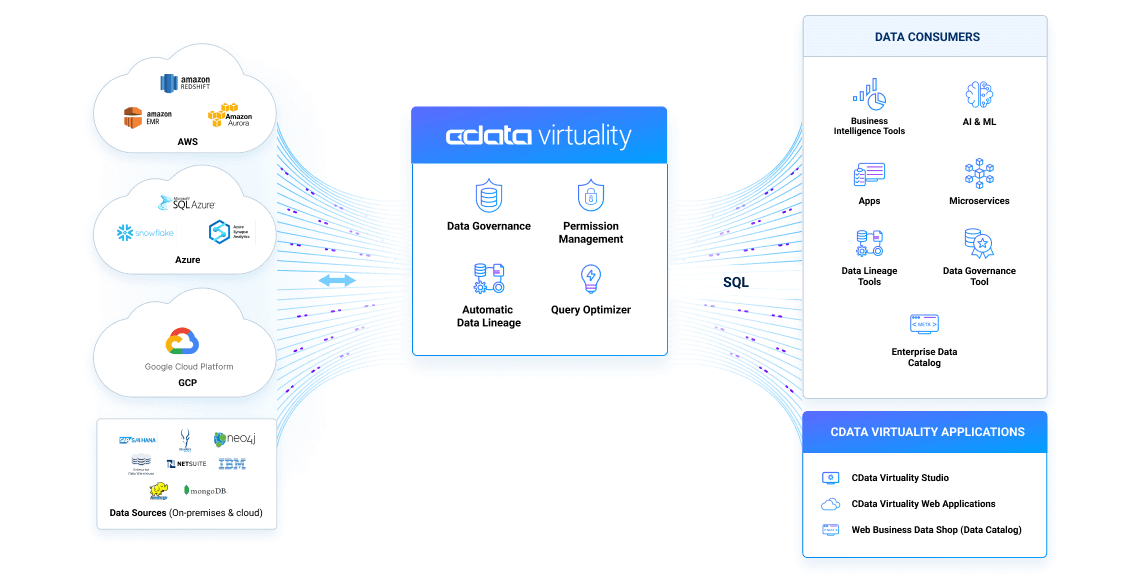
Benefits of a hybrid- or multi-cloud environment enabled by CData Virtuality
Fully integrated data landscape
All data sources, whether in private or public cloud or on-premises can easily be integrated with CData Virtuality providing a single layer for data access and delivery. This way, data silos can be eliminated or avoided.
Easy data movement or live access
Support for both real-time connectivity and data replication with CData Virtuality. Easily lift data into the cloud to exchange between different storage systems. Intelligent connectors optimize extract and load jobs or facilitate live data access in your favorite reporting tools.
Transparency and traceability
Features such as automatic data lineage, column-level data lineage, and persuasive audit trails in CData Virtuality give you full control over your data. With just one click, you can check where the data comes from, how it was manipulated, and by whom.
Data protection and compliance
A granular permission layer (schema, table, column-, and row-level), built-in user/role-based permission system, flexible data masking, versioning for custom metadata, and other features in CData Virtuality ensure a high level of data security. Ensure users solely access relevant data and gain visibility into who is modifying data models.





