Discover how a bimodal integration strategy can address the major data management challenges facing your organization today.
Get the Report →Connect to Okta Data in DigitalSuite Studio through RunMyProcess DSEC
Use Arkobi Digital's low-code cloud native platform RunMyProcess's DigitalSuite EnterpriseConnect (DSEC) to connect to Okta.
The CData JDBC Driver for Okta implements JDBC Standards and enables a applications ranging from BI to IDE to connect with Okta. In this article, we describe how to connect to Okta data from Arkobi Digital RunMyProcess's DSEC and connect to Okta in RunMyProcess.
Setting up EnterpriseConnect Agent
Configure the EnterpriseConnect Agent following the EnterpriseConnect page in the RunMyProcess documentation.
Setting up JDBC Adapter
The JDBC Adapter section describes the steps to connect to RDBMS through JDBC. Follow the steps and open the JDBC.config file.
- Create a JSON entry for the CData JDBC Driver for Okta, e.g.
Okta = { "sqlDriver" : "...", "sqlSource" : "...", "sqlDriverPath" : "..." } - Set the "sqlDriver" field to the Class name for the CData JDBC Driver, e.g.
cdata.jdbc.okta.OktaDriver - Set the "sqlSource" field to a JDBC URL for connecting to Okta, e.g.
jdbc:okta:Domain=dev-44876464.okta.com;InitiateOAuth=GETANDREFRESHBuilt-in Connection String Designer
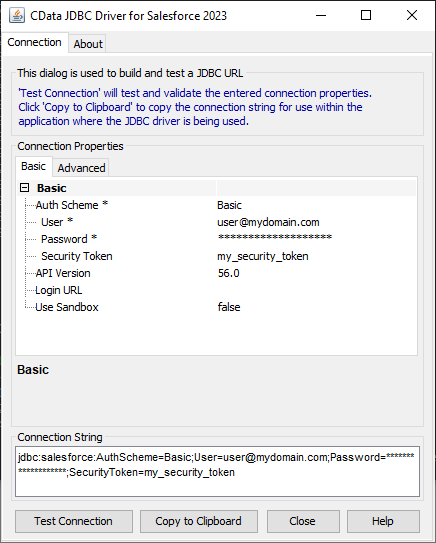
For assistance in constructing the JDBC URL, use the connection string designer built into the Okta JDBC Driver. Either double-click the JAR file or execute the jar file from the command-line.
java -jar cdata.jdbc.okta.jarFill in the connection properties and copy the connection string to the clipboard.
To connect to Okta, set the Domain connection string property to your Okta domain.
You will use OAuth to authenticate with Okta, so you need to create a custom OAuth application.
Creating a Custom OAuth Application
From your Okta account:
- Sign in to your Okta developer edition organization with your administrator account.
- In the Admin Console, go to Applications > Applications.
- Click Create App Integration.
- For the Sign-in method, select OIDC - OpenID Connect.
- For Application type, choose Web Application.
- Enter a name for your custom application.
- Set the Grant Type to Authorization Code. If you want the token to be automatically refreshed, also check Refresh Token.
- Set the callback URL:
- For desktop applications and headless machines, use http://localhost:33333 or another port number of your choice. The URI you set here becomes the CallbackURL property.
- For web applications, set the callback URL to a trusted redirect URL. This URL is the web location the user returns to with the token that verifies that your application has been granted access.
- In the Assignments section, either select Limit access to selected groups and add a group, or skip group assignment for now.
- Save the OAuth application.
- The application's Client Id and Client Secret are displayed on the application's General tab. Record these for future use. You will use the Client Id to set the OAuthClientId and the Client Secret to set the OAuthClientSecret.
- Check the Assignments tab to confirm that all users who must access the application are assigned to the application.
- On the Okta API Scopes tab, select the scopes you wish to grant to the OAuth application. These scopes determine the data that the app has permission to read, so a scope for a particular view must be granted for the driver to have permission to query that view. To confirm the scopes required for each view, see the view-specific pages in Data Model < Views in the Help documentation.
![Using the built-in connection string designer to generate a JDBC URL (Salesforce is shown.)]()
- Set the "sqlDriverPath" field to the name of the CData JDBC Driver JAR file, e.g.
cdata.jdbc.okta.jar
Sample JDBC.config File
#DBAgent Configuration
Okta = {"sqlDriver" : "cdata.jdbc.okta.OktaDriver", "sqlSource" = "jdbc:okta:Domain=dev-44876464.okta.com;","sqlDriverPath" = "cdata.jdbc.okta.jar" }
Put the JDBC driver JAR file (cdata.jdbc.okta.jar) into the same directory as unified-adapter-[version].jar.
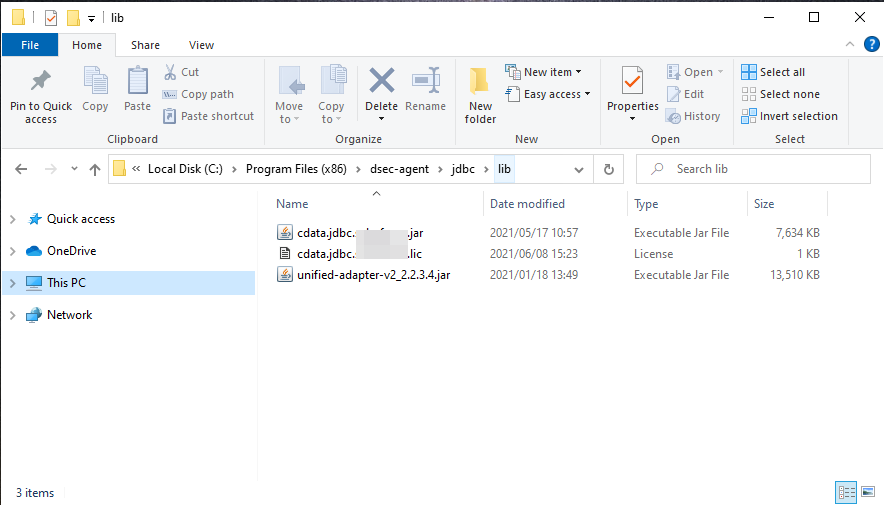
Note: Make sure to put the CData license file (cdata.jdbc.okta.lic) into the same directory. Since the license is generated based on the unique identifier of the machine where the product in installed, you will need an offline activation if you want to put the file on another machine.
Starting DigitalSuite EnterpriseConnect Agent
In Windows, start RunMyProcess DigitalSuite EnterpriseConnect Agent in Windows services. To start the application through command line, see Starting the EnterpriseConnect Agent in the RunMyProcess documents.
Starting the JDBC Adapter
Start the JDBC Adapter from runAdapter.bat. Once the Adapter is running, you can access the application through the agent address (e.g. 127.0.0.1:8080). Below is an example executing the command in Windows.
... > java -Djava.util.logging.config.file=./log.properties -cp lib/* org.runmyprocess.sec2.AdapterHandler :
2021-06-09 14:37:58|INFO|correlationId=|Searching for config file...
2021-06-09 14:37:58|INFO|correlationId=|Adapter Handler started with [JDBC] configuration
2021-06-09 14:37:59|INFO|correlationId=|agent address: 127.0.0.1:8080
2021-06-09 14:38:00.251:INFO::ConnectionThread: Logging initialized @1820ms to org.eclipse.jetty.util.log.StdErrLog
2021-06-09 14:38:00|INFO|correlationId=|onConnect() websocket connection between Agent and Adapter established
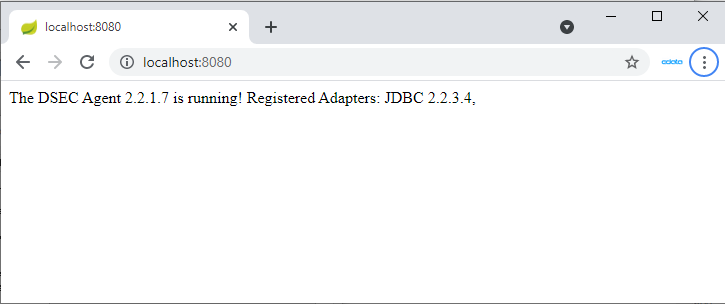
Once the DigitalSuite EnterpriseConnect Agent and JDBC Adapter are running, access http://localhost:(specified-port-number)/ through your browser to open the page shown below.
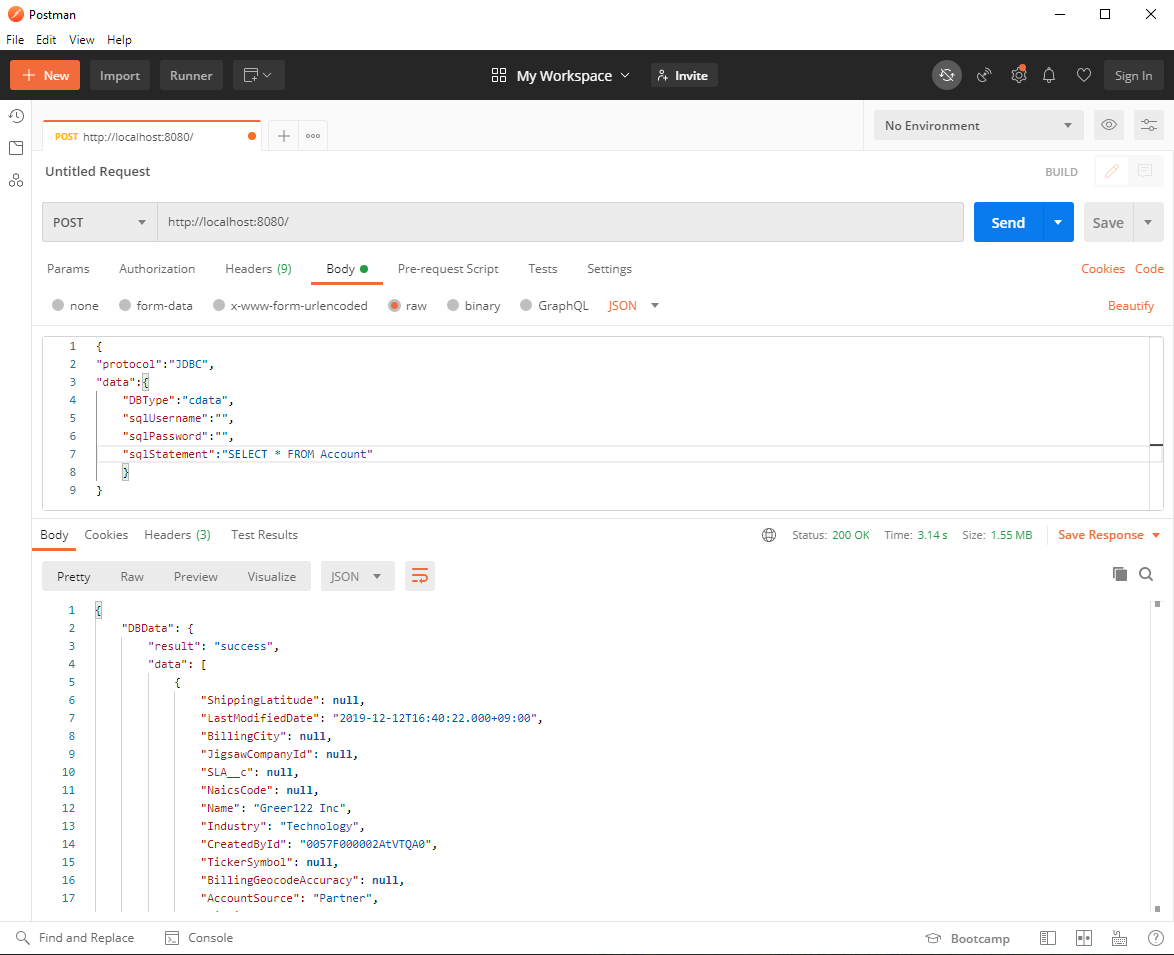
Check the availability of the JDBC Adapter using tools such as Postman or cURL. Here, we use Postman to send the HTTP POST request.
Configure the RequestHeader as follows:
Content-Type application/json
Configure the RequestBody as follows:
{
"protocol":"JDBC",
"data":{
"DBType":"Okta",
"sqlUsername":"",
"sqlPassword":"",
"sqlStatement":"SELECT * FROM Users"
}
}
If the JDBC.config file contains credential information, sqlUsername and sqlPassword can be left empty. If you are not sure of the table name, you can retrieve the list of tables using the request SELECT * FROM sys_tables
The request is successful if the Status is 200 and the Body contains Okta data in JSON format.
Connect to Okta through DSEC Agent in DigitalSuite Studio
Create a DigitalSuite Studio project and then create a Provider in the project.
- URL: The URL for accessing JDBC Agent (e.g. http:localhost:8080/)
- Authentication Scheme: Login/password
- Login: The value from agent.user in the application.properties file
- Password: agent.password in the application.properties file
- Secured: Checked
- Use DigitalSuite EnterpriseConnect: Checked
- With domain: The value from agent.domain in application.properties file
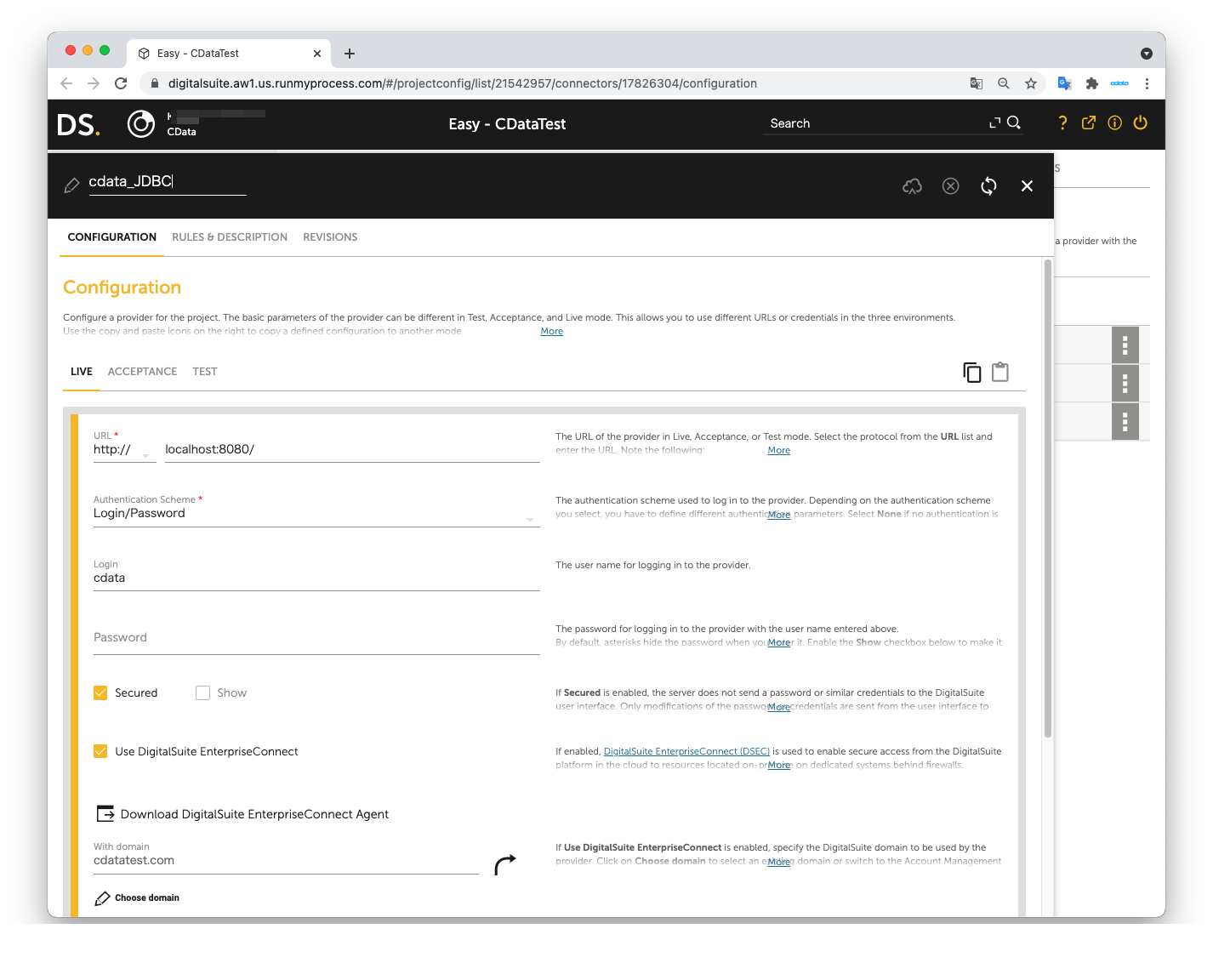
Next, create a Connector in the Provider.
- Connector URL: Leave this empty
- Architecture: REST/XML-RPC
- Method: POST
- Result format: JSON
- Accept media type: application/json
- Character set: Automatic
- Content: Same as the Request body used in the JDBC Adapter
- Content type: application/json
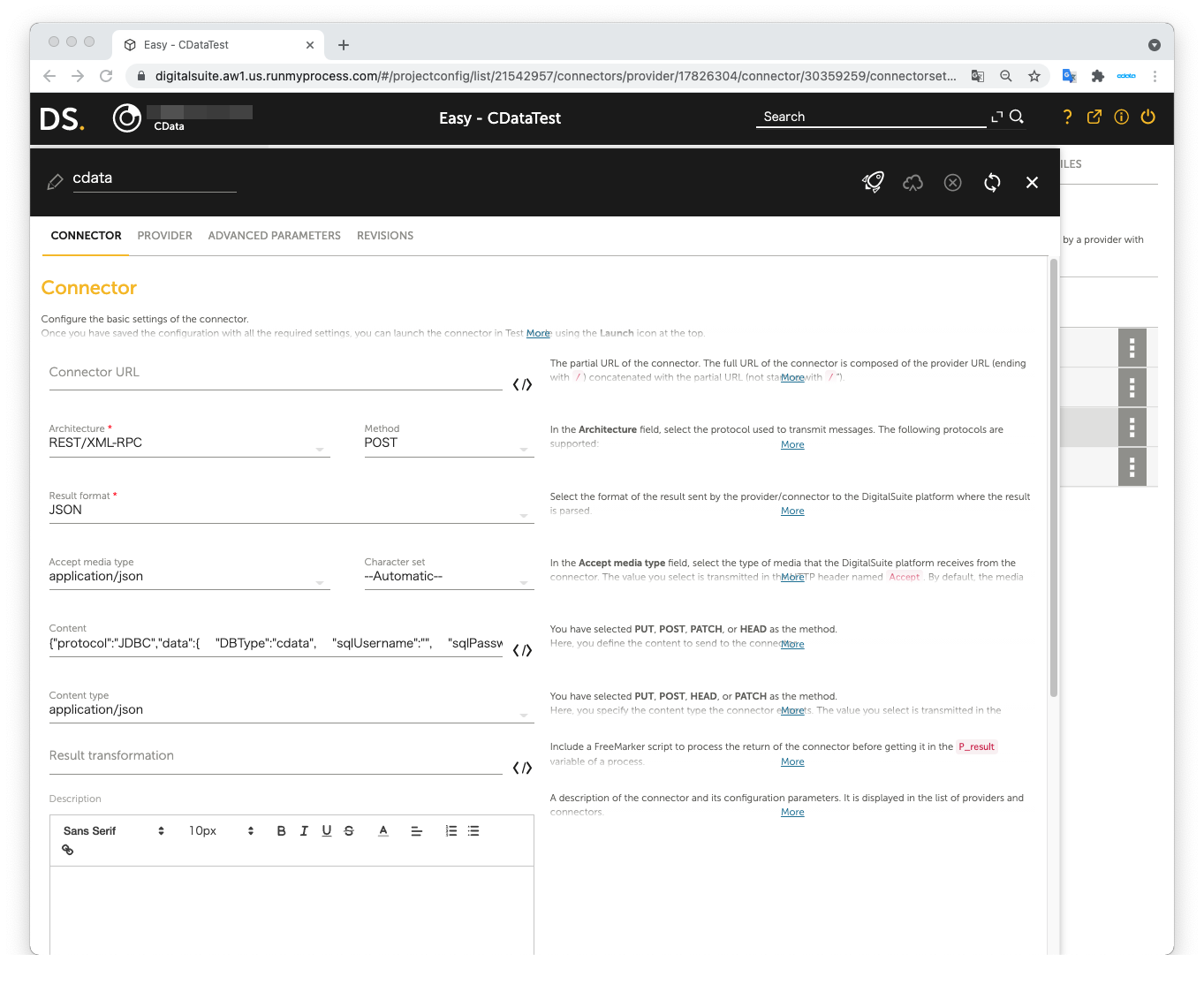
The JSON data we used as the Request body in JDBC Adapter:
{
"protocol":"JDBC",
"data":{
"DBType":"Okta",
"sqlUsername":"",
"sqlPassword":"",
"sqlStatement":"SELECT * FROM Users"
}
}
Open Launch Test to perform the test. The test is successful if Okta data is shown in Result on the right pane.
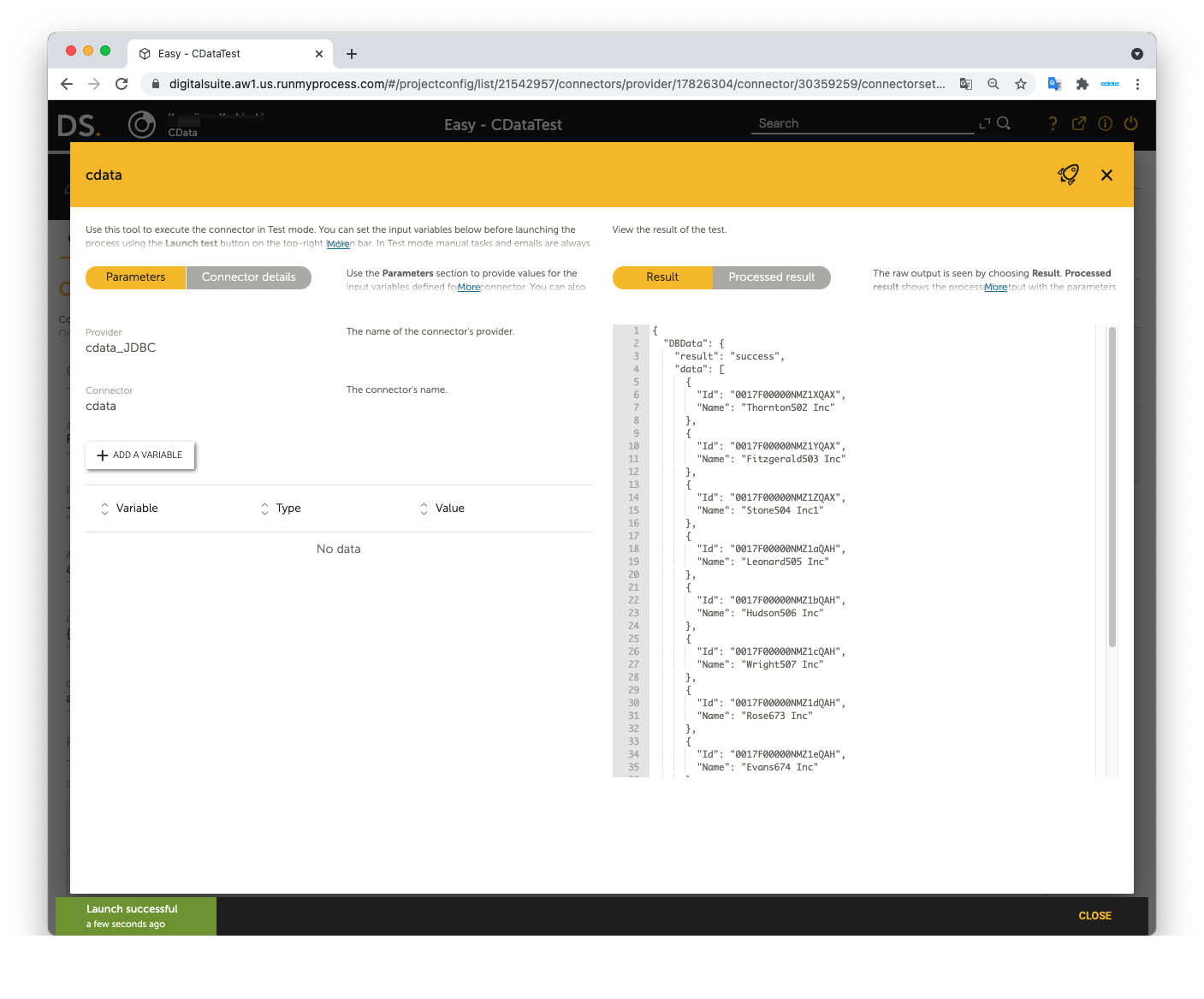
Now you can use Okta data in RunMyProcess DigitalSuite Studio through DSEC.
For the detailed information on supported SQL commands, refer to the SQL Compliance section in our help documentation. For information on tables, refer to the Data Model section.