Discover how a bimodal integration strategy can address the major data management challenges facing your organization today.
Get the Report →Automate Tasks in Power Automate Using the CData API Server and Presto ADO.NET Provider
Automate actions like sending emails to a contact list, posting to social media, or syncing CRM and ERP.
Power Automate (Microsoft Flow) makes it easy to automate tasks that involve data from multiple systems, on premises or in the cloud. With the CData API Server and Presto ADO.NET Provider (or any of 200+ other ADO.NET Providers), line-of-business users have a native way to create actions based on Presto triggers in Power Automate; the API Server makes it possible for SaaS applications like Power Automate to integrate seamlessly with Presto data through data access standards like Swagger and OData. This article shows how to use wizards in Power Automate and the API Server for Presto to create a trigger -- entities that match search criteria -- and send an email based on the results.
Set Up the API Server
Follow the steps below to begin producing secure and Swagger-enabled Presto APIs:
Deploy
The API Server runs on your own server. On Windows, you can deploy using the stand-alone server or IIS. On a Java servlet container, drop in the API Server WAR file. See the help documentation for more information and how-tos.
The API Server is also easy to deploy on Microsoft Azure, Amazon EC2, and Heroku.
Connect to Presto
After you deploy, provide authentication values and other connection properties by clicking Settings -> Connections in the API Server administration console. You can then choose the entities you want to allow the API Server access to by clicking Settings -> Resources.
Set the Server and Port connection properties to connect, in addition to any authentication properties that may be required.
To enable TLS/SSL, set UseSSL to true.
Authenticating with LDAP
In order to authenticate with LDAP, set the following connection properties:
- AuthScheme: Set this to LDAP.
- User: The username being authenticated with in LDAP.
- Password: The password associated with the User you are authenticating against LDAP with.
Authenticating with Kerberos
In order to authenticate with KERBEROS, set the following connection properties:
- AuthScheme: Set this to KERBEROS.
- KerberosKDC: The Kerberos Key Distribution Center (KDC) service used to authenticate the user.
- KerberosRealm: The Kerberos Realm used to authenticate the user with.
- KerberosSPN: The Service Principal Name for the Kerberos Domain Controller.
- KerberosKeytabFile: The Keytab file containing your pairs of Kerberos principals and encrypted keys.
- User: The user who is authenticating to Kerberos.
- Password: The password used to authenticate to Kerberos.
You will also need to enable CORS and define the following sections on the Settings -> Server page. As an alternative, you can select the option to allow all domains without '*'.
- Access-Control-Allow-Origin: Set this to a value of '*' or specify the domains that are allowed to connect.
- Access-Control-Allow-Methods: Set this to a value of "GET,PUT,POST,OPTIONS".
- Access-Control-Allow-Headers: Set this to "x-ms-client-request-id, authorization, content-type".
Authorize API Server Users
After determining the OData services you want to produce, authorize users by clicking Settings -> Users. The API Server uses authtoken-based authentication and supports the major authentication schemes. You can authenticate as well as encrypt connections with SSL. Access can also be restricted by IP address; access is restricted to only the local machine by default.
For simplicity, we will allow the authtoken for API users to be passed in the URL. You will need to add a setting in the Application section of the settings.cfg file, located in the data directory. On Windows, this is the app_data subfolder in the application root. In the Java edition, the location of the data directory depends on your operation system:
- Windows: C:\ProgramData\CData
- Unix or Mac OS X: ~/cdata
[Application]
AllowAuthtokenInURL = true
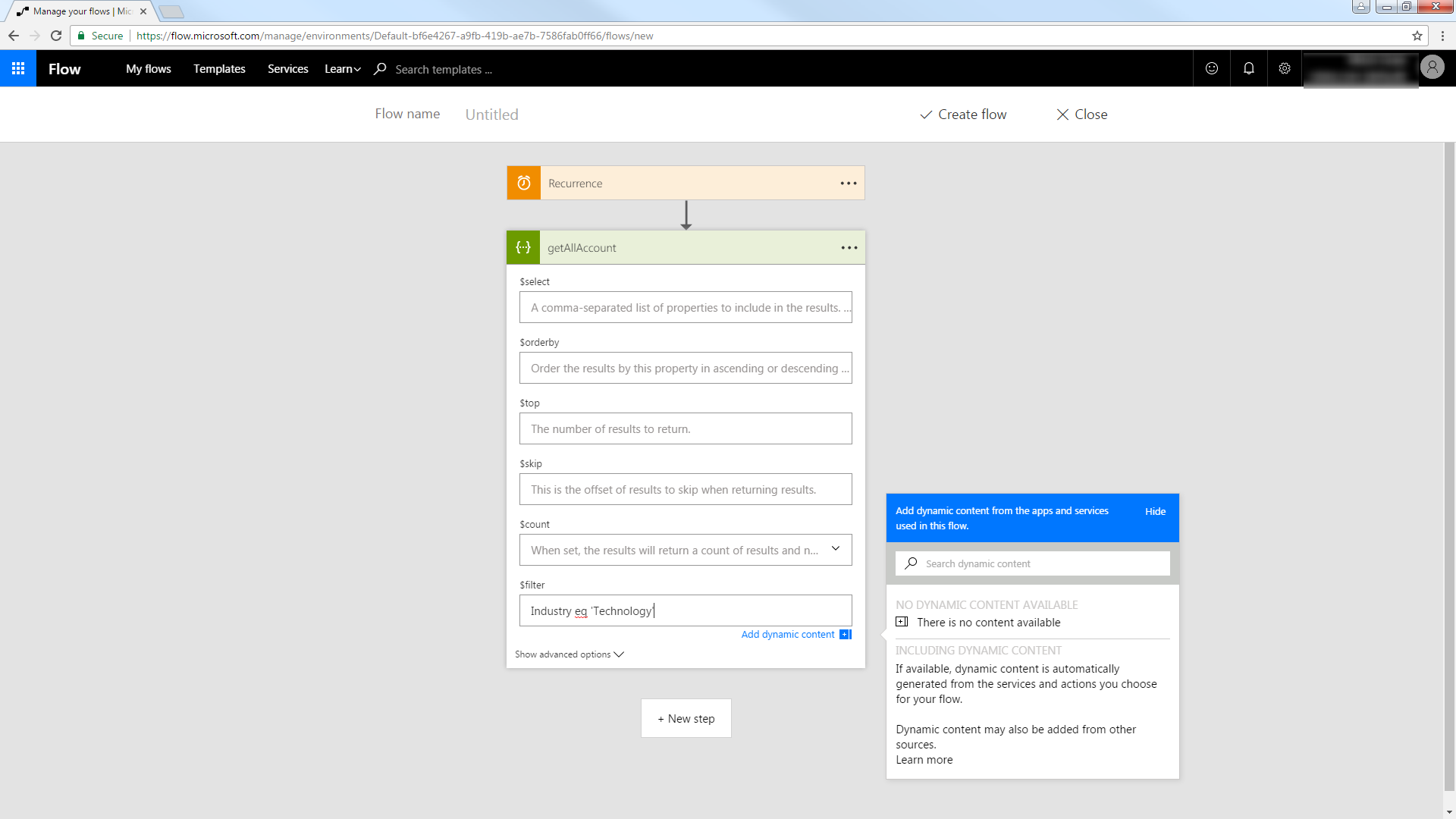
Add Presto Data to a Flow
You can use the built-in HTTP + Swagger connector to use a wizard to design a Presto process flow:
- In Power Automate, click My Flows -> Create from Blank.
- Select the Recurrence action and select a time interval for sending emails. This article uses 1 day.
- Add an HTTP + Swagger action by searching for Swagger.
- Enter the URL to the Swagger metadata document:
https://MySite:MyPort/api.rsc/@MyAuthtoken/$oas - Select the "Return Customer" operation.
Build the OData query to retrieve Presto data. This article defines the following OData filter expression in the $filter box:
Id eq '123456789'
See the API Server help documentation for more on filtering and examples of the supported OData.
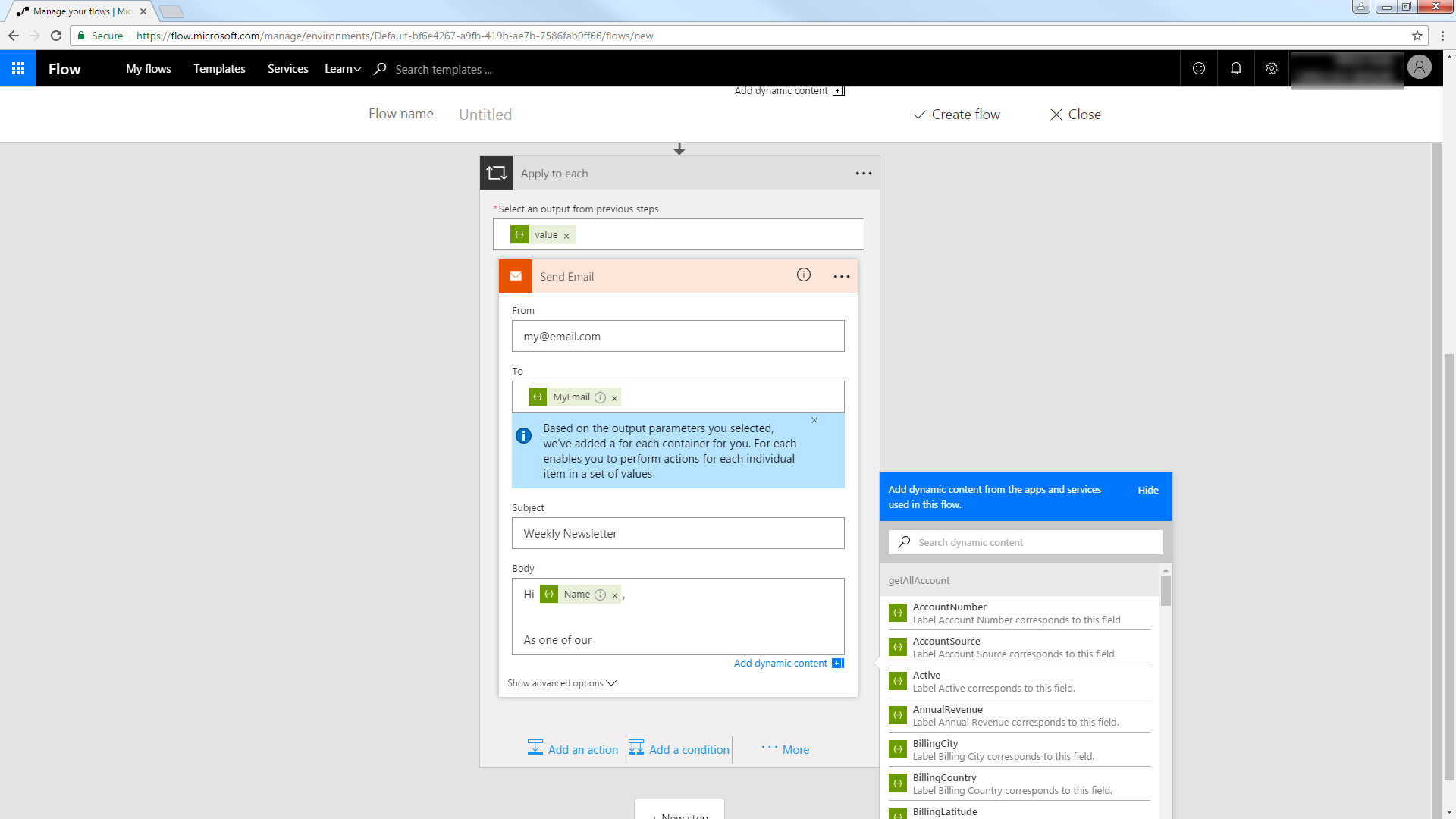
Trigger an Action
You can now work with Customer entities in your process flow. Follow the steps to send an automated email:
- Add an SMTP - Send Email action.
- Enter the address and credentials for the SMTP server and name the connection. Be sure to enable encryption if supported by your server.
- Enter the message headers and body. You can add Presto columns in these boxes.
![An email to be populated with results from an OData query. (Salesforce is shown.)]()