Discover how a bimodal integration strategy can address the major data management challenges facing your organization today.
Get the Report →Edit and Search Amazon Athena External Objects
Use the API Server to securely provide OData feeds of Amazon Athena data to smart devices and cloud-based applications. Use the API Server and Salesforce Connect to create Amazon Athena objects that you can access from apps and the dashboard.
The CData API Server, when paired with the (or any of 200+ other ADO.NET Providers), enables you to access Amazon Athena data from cloud-based applications like the Salesforce console and mobile applications like the Salesforce1 Mobile App. In this article, you will use the API Server and Salesforce Connect to access Amazon Athena external objects alongside standard Salesforce objects.
Set Up the API Server
Follow the steps below to begin producing secure Amazon Athena OData services:
Deploy
The API Server runs on your own server. On Windows, you can deploy using the stand-alone server or IIS. On a Java servlet container, drop in the API Server WAR file. See the help documentation for more information and how-tos. You can find guides to deploying the API Server on Azure, Amazon EC2, and Heroku in the CData KB.
Connect to Amazon Athena
After you deploy the API Server and the , provide authentication values and other connection properties needed to connect to Amazon Athena by clicking Settings -> Connection and adding a new connection in the API Server administration console.
Authenticating to Amazon Athena
To authorize Amazon Athena requests, provide the credentials for an administrator account or for an IAM user with custom permissions: Set AccessKey to the access key Id. Set SecretKey to the secret access key.
Note: Though you can connect as the AWS account administrator, it is recommended to use IAM user credentials to access AWS services.
Obtaining the Access Key
To obtain the credentials for an IAM user, follow the steps below:
- Sign into the IAM console.
- In the navigation pane, select Users.
- To create or manage the access keys for a user, select the user and then select the Security Credentials tab.
To obtain the credentials for your AWS root account, follow the steps below:
- Sign into the AWS Management console with the credentials for your root account.
- Select your account name or number and select My Security Credentials in the menu that is displayed.
- Click Continue to Security Credentials and expand the Access Keys section to manage or create root account access keys.
Authenticating from an EC2 Instance
If you are using the CData Data Provider for Amazon Athena 2018 from an EC2 Instance and have an IAM Role assigned to the instance, you can use the IAM Role to authenticate. To do so, set UseEC2Roles to true and leave AccessKey and SecretKey empty. The CData Data Provider for Amazon Athena 2018 will automatically obtain your IAM Role credentials and authenticate with them.
Authenticating as an AWS Role
In many situations it may be preferable to use an IAM role for authentication instead of the direct security credentials of an AWS root user. An AWS role may be used instead by specifying the RoleARN. This will cause the CData Data Provider for Amazon Athena 2018 to attempt to retrieve credentials for the specified role. If you are connecting to AWS (instead of already being connected such as on an EC2 instance), you must additionally specify the AccessKey and SecretKey of an IAM user to assume the role for. Roles may not be used when specifying the AccessKey and SecretKey of an AWS root user.
Authenticating with MFA
For users and roles that require Multi-factor Authentication, specify the MFASerialNumber and MFAToken connection properties. This will cause the CData Data Provider for Amazon Athena 2018 to submit the MFA credentials in a request to retrieve temporary authentication credentials. Note that the duration of the temporary credentials may be controlled via the TemporaryTokenDuration (default 3600 seconds).
Connecting to Amazon Athena
In addition to the AccessKey and SecretKey properties, specify Database, S3StagingDirectory and Region. Set Region to the region where your Amazon Athena data is hosted. Set S3StagingDirectory to a folder in S3 where you would like to store the results of queries.
If Database is not set in the connection, the data provider connects to the default database set in Amazon Athena.
You can then choose the Amazon Athena entities you want to allow the API Server access to by clicking Settings -> Resources.
Authorize API Server Users
After determining the OData services you want to produce, authorize users by clicking Settings -> Users. The API Server uses authtoken-based authentication and supports the major authentication schemes. Access can also be restricted based on IP address; by default, only connections to the local machine are allowed. You can authenticate as well as encrypt connections with SSL.
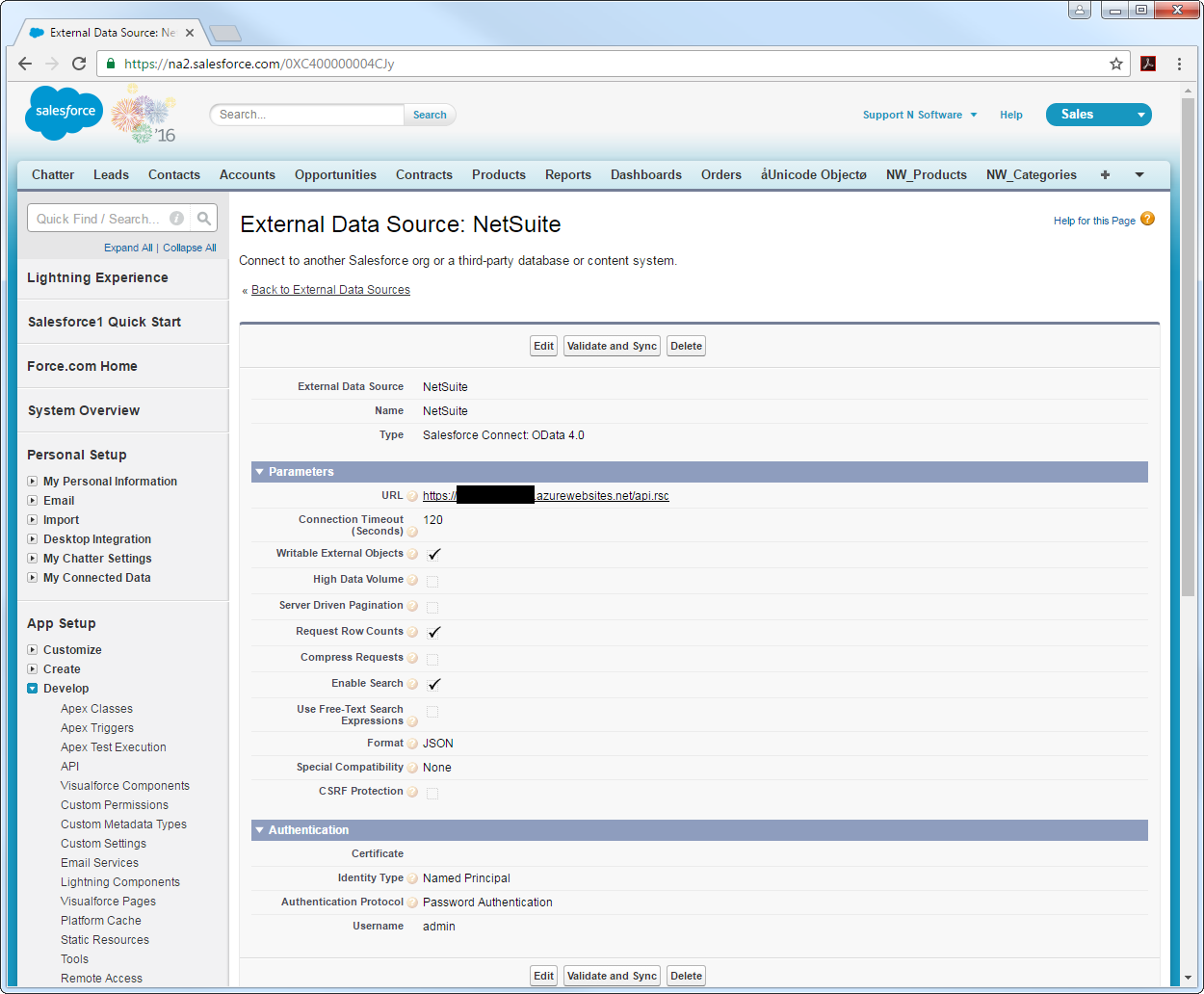
Connect to Amazon Athena Data as an External Data Source
Follow the steps below to connect to the feed produced by the API Server.
- Log into Salesforce and click Setup -> Develop -> External Data Sources.
- Click New External Data Source.
- Enter values for the following properties:
- External Data Source: Enter a label to be used in list views and reports.
- Name: Enter a unique identifier.
- Type: Select the option "Salesforce Connect: OData 4.0".
URL: Enter the URL to the OData endpoint of the API Server. The format of the OData URL is https://your-server:your-port/api.rsc.
Note that plain-text is suitable for only testing; for production, use TLS.
- Select the Writable External Objects option.
Select JSON in the Format menu.
- In the Authentication section, set the following properties:
- Identity Type: If all members of your organization will use the same credentials to access the API Server, select "Named Principal". If the members of your organization will connect with their own credentials, select "Per User".
- Authentication Protocol: Select Password Authentication to use basic authentication.
- Certificate: Enter or browse to the certificate to be used to encrypt and authenticate communications from Salesforce to your server.
- Username: Enter the username for a user known to the API Server.
- Password: Enter the user's authtoken.
Synchronize Amazon Athena Objects
After you have created the external data source, follow the steps below to create Amazon Athena external objects that reflect any changes in the data source. You will synchronize the definitions for the Amazon Athena external objects with the definitions for Amazon Athena tables.
- Click the link for the external data source you created.
- Click Validate and Sync.
- Select the Amazon Athena tables you want to work with as external objects.

Access Amazon Athena Data as Salesforce Objects
After adding Amazon Athena data as an external data source and syncing Amazon Athena tables with Amazon Athena external objects, you can use the external objects just as you would standard Salesforce objects.
-
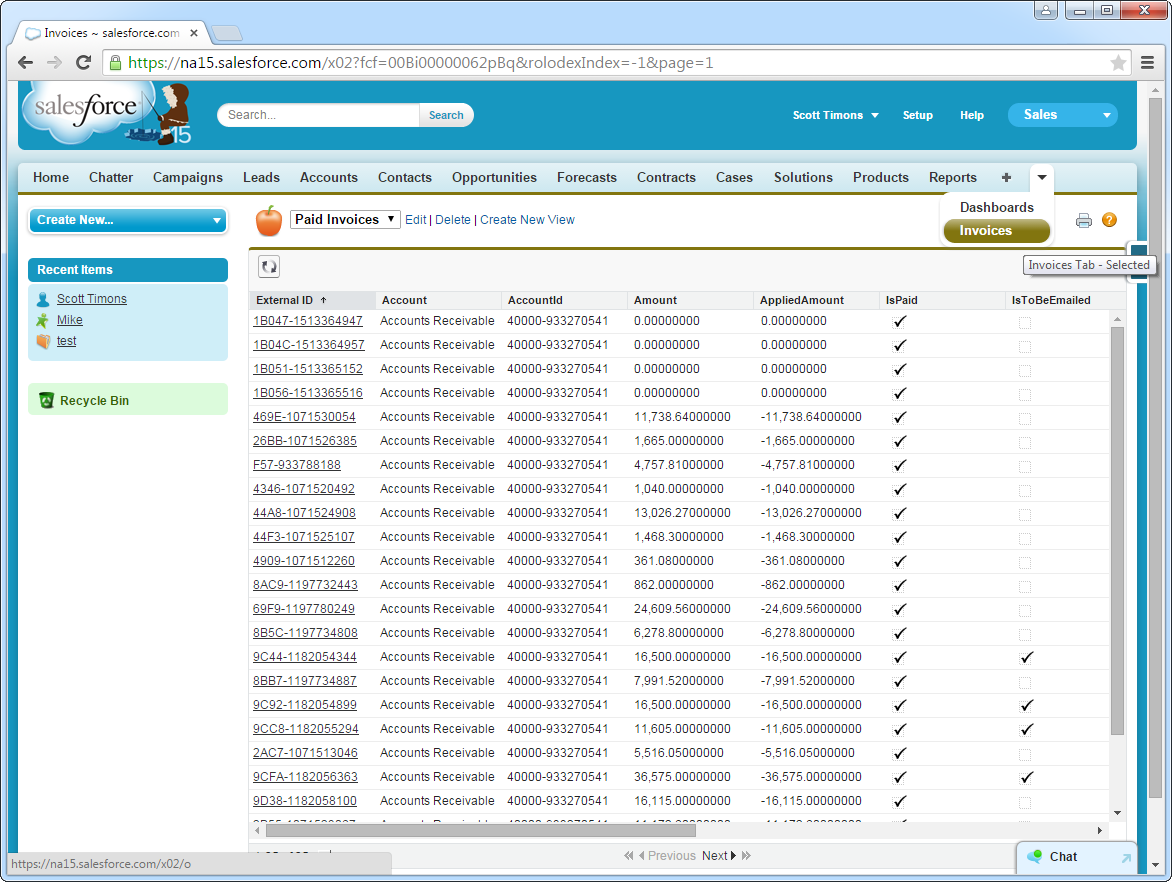
Create a new tab with a filter list view:
![A filtered list view shown on a custom tab. (NetSuite Invoices are shown.)]()
-
Display related lists of Amazon Athena external objects alongside standard Salesforce objects:
![A related list that shows an indirect lookup relationship, which links a child external object to a parent standard object. (Salesforce accounts and associated NetSuite invoices are shown.)]()
-
Create, read, update, and delete Amazon Athena objects from tabs on the Salesforce dashboard:
![Editing external objects from the Salesforce dashboard. (NetSuite Employees are shown.)]()
Troubleshooting
You can use the following checklist to avoid typical connection problems:
- Ensure that your server has a publicly accessible IP address. Related to this check, but one layer up, at the operating system layer, you will also need to ensure that your firewall has an opening for the port the API Server is running on. At the application layer, ensure that you have added trusted IP addresses on the Settings -> Security tab of the administration console.
- Ensure that you are using a connection secured by an SSL certificate from a commercial, trusted CA. Salesforce does not currently accept self-signed certificates or internal CAs.
Ensure that the server you are hosting the API Server on is using TLS 1.1 or above. If you are using the .NET API Server, you can accomplish this by using the .NET API Server's embedded server.
If you are using IIS, TLS 1.1 and 1.2 are supported but not enabled by default. To enable these protocols, refer to the how-to on MSDN and the Microsoft technical reference.
If you are using the Java edition, note that TLS 1.2 is enabled by default in Java 8 but not in Java 6 or 7. If you are using these earlier versions, you can refer to this this Oracle how-to.