Discover how a bimodal integration strategy can address the major data management challenges facing your organization today.
Get the Report →Automate Tasks in Power Automate Using the CData API Server and Amazon Athena ADO.NET Provider
Automate actions like sending emails to a contact list, posting to social media, or syncing CRM and ERP.
Power Automate (Microsoft Flow) makes it easy to automate tasks that involve data from multiple systems, on premises or in the cloud. With the CData API Server and Amazon Athena ADO.NET Provider (or any of 200+ other ADO.NET Providers), line-of-business users have a native way to create actions based on Amazon Athena triggers in Power Automate; the API Server makes it possible for SaaS applications like Power Automate to integrate seamlessly with Amazon Athena data through data access standards like Swagger and OData. This article shows how to use wizards in Power Automate and the API Server for Amazon Athena to create a trigger -- entities that match search criteria -- and send an email based on the results.
Set Up the API Server
Follow the steps below to begin producing secure and Swagger-enabled Amazon Athena APIs:
Deploy
The API Server runs on your own server. On Windows, you can deploy using the stand-alone server or IIS. On a Java servlet container, drop in the API Server WAR file. See the help documentation for more information and how-tos.
The API Server is also easy to deploy on Microsoft Azure, Amazon EC2, and Heroku.
Connect to Amazon Athena
After you deploy, provide authentication values and other connection properties by clicking Settings -> Connections in the API Server administration console. You can then choose the entities you want to allow the API Server access to by clicking Settings -> Resources.
Authenticating to Amazon Athena
To authorize Amazon Athena requests, provide the credentials for an administrator account or for an IAM user with custom permissions: Set AccessKey to the access key Id. Set SecretKey to the secret access key.
Note: Though you can connect as the AWS account administrator, it is recommended to use IAM user credentials to access AWS services.
Obtaining the Access Key
To obtain the credentials for an IAM user, follow the steps below:
- Sign into the IAM console.
- In the navigation pane, select Users.
- To create or manage the access keys for a user, select the user and then select the Security Credentials tab.
To obtain the credentials for your AWS root account, follow the steps below:
- Sign into the AWS Management console with the credentials for your root account.
- Select your account name or number and select My Security Credentials in the menu that is displayed.
- Click Continue to Security Credentials and expand the Access Keys section to manage or create root account access keys.
Authenticating from an EC2 Instance
If you are using the CData Data Provider for Amazon Athena 2018 from an EC2 Instance and have an IAM Role assigned to the instance, you can use the IAM Role to authenticate. To do so, set UseEC2Roles to true and leave AccessKey and SecretKey empty. The CData Data Provider for Amazon Athena 2018 will automatically obtain your IAM Role credentials and authenticate with them.
Authenticating as an AWS Role
In many situations it may be preferable to use an IAM role for authentication instead of the direct security credentials of an AWS root user. An AWS role may be used instead by specifying the RoleARN. This will cause the CData Data Provider for Amazon Athena 2018 to attempt to retrieve credentials for the specified role. If you are connecting to AWS (instead of already being connected such as on an EC2 instance), you must additionally specify the AccessKey and SecretKey of an IAM user to assume the role for. Roles may not be used when specifying the AccessKey and SecretKey of an AWS root user.
Authenticating with MFA
For users and roles that require Multi-factor Authentication, specify the MFASerialNumber and MFAToken connection properties. This will cause the CData Data Provider for Amazon Athena 2018 to submit the MFA credentials in a request to retrieve temporary authentication credentials. Note that the duration of the temporary credentials may be controlled via the TemporaryTokenDuration (default 3600 seconds).
Connecting to Amazon Athena
In addition to the AccessKey and SecretKey properties, specify Database, S3StagingDirectory and Region. Set Region to the region where your Amazon Athena data is hosted. Set S3StagingDirectory to a folder in S3 where you would like to store the results of queries.
If Database is not set in the connection, the data provider connects to the default database set in Amazon Athena.
You will also need to enable CORS and define the following sections on the Settings -> Server page. As an alternative, you can select the option to allow all domains without '*'.
- Access-Control-Allow-Origin: Set this to a value of '*' or specify the domains that are allowed to connect.
- Access-Control-Allow-Methods: Set this to a value of "GET,PUT,POST,OPTIONS".
- Access-Control-Allow-Headers: Set this to "x-ms-client-request-id, authorization, content-type".
Authorize API Server Users
After determining the OData services you want to produce, authorize users by clicking Settings -> Users. The API Server uses authtoken-based authentication and supports the major authentication schemes. You can authenticate as well as encrypt connections with SSL. Access can also be restricted by IP address; access is restricted to only the local machine by default.
For simplicity, we will allow the authtoken for API users to be passed in the URL. You will need to add a setting in the Application section of the settings.cfg file, located in the data directory. On Windows, this is the app_data subfolder in the application root. In the Java edition, the location of the data directory depends on your operation system:
- Windows: C:\ProgramData\CData
- Unix or Mac OS X: ~/cdata
[Application]
AllowAuthtokenInURL = true
Add Amazon Athena Data to a Flow
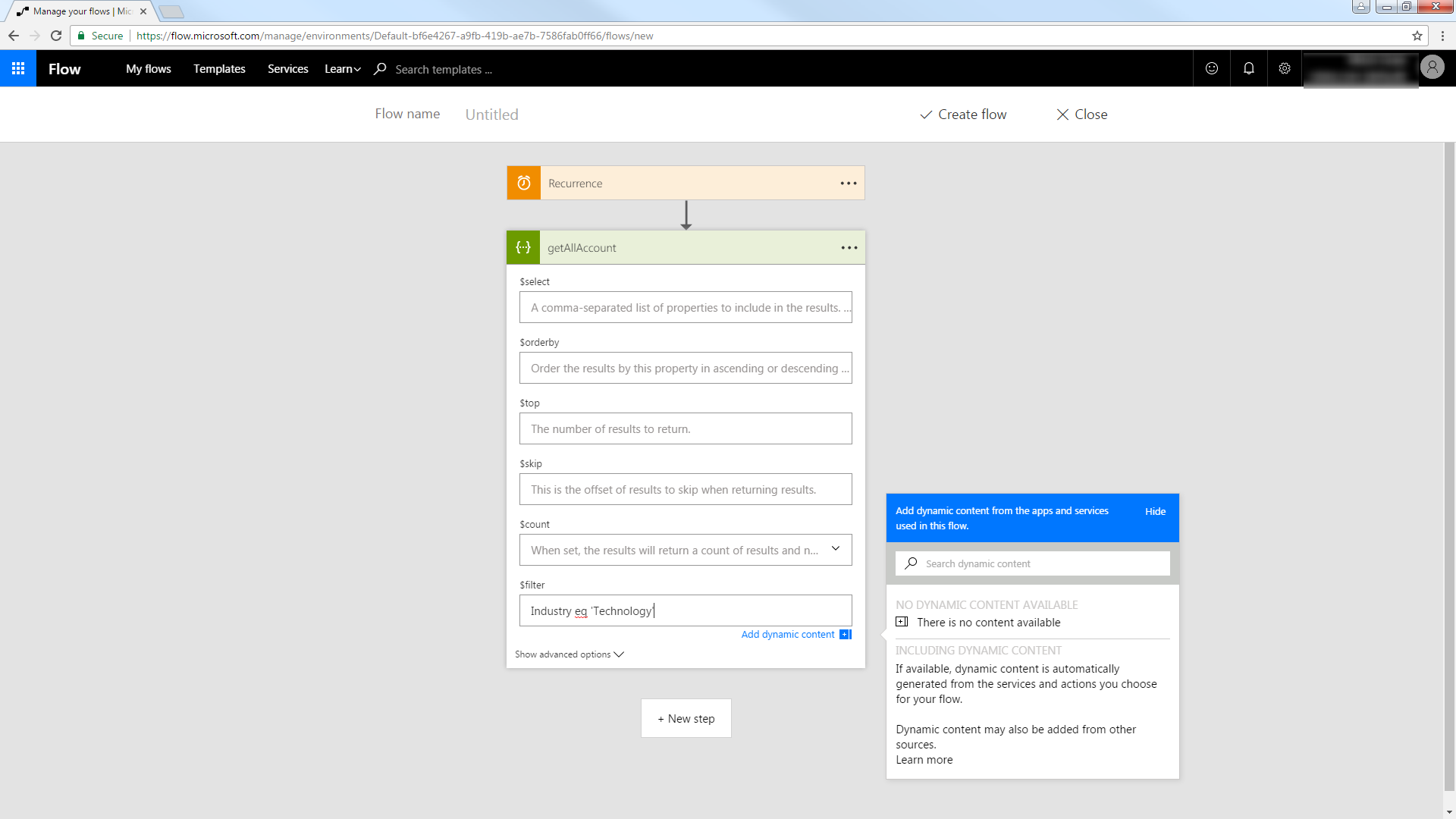
You can use the built-in HTTP + Swagger connector to use a wizard to design a Amazon Athena process flow:
- In Power Automate, click My Flows -> Create from Blank.
- Select the Recurrence action and select a time interval for sending emails. This article uses 1 day.
- Add an HTTP + Swagger action by searching for Swagger.
- Enter the URL to the Swagger metadata document:
https://MySite:MyPort/api.rsc/@MyAuthtoken/$oas - Select the "Return Customers" operation.
Build the OData query to retrieve Amazon Athena data. This article defines the following OData filter expression in the $filter box:
CustomerId eq '12345'
See the API Server help documentation for more on filtering and examples of the supported OData.
Trigger an Action
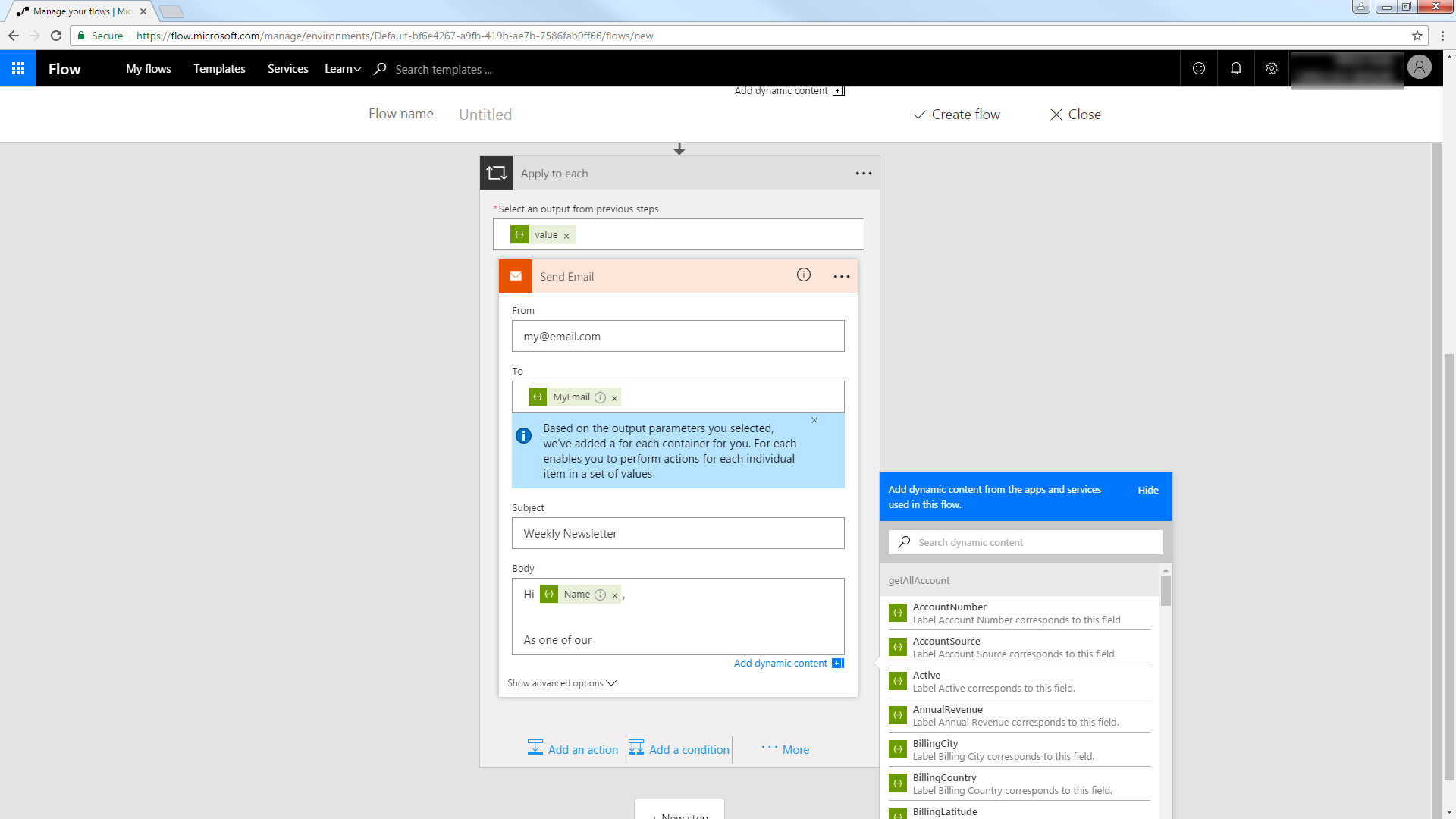
You can now work with Customers entities in your process flow. Follow the steps to send an automated email:
- Add an SMTP - Send Email action.
- Enter the address and credentials for the SMTP server and name the connection. Be sure to enable encryption if supported by your server.
- Enter the message headers and body. You can add Amazon Athena columns in these boxes.
![An email to be populated with results from an OData query. (Salesforce is shown.)]()