Discover how a bimodal integration strategy can address the major data management challenges facing your organization today.
Get the Report →Create Amazon Athena-Connected Visualizations in Klipfolio
Use CData Connect Cloud to connect to Amazon Athena Data from Klipfolio and build custom visualizations using live Amazon Athena data.
Klipfolio is an online dashboard platform designed to create real-time business dashboards, whether for your team or clients. When combined with CData Connect Cloud, you gain immediate cloud-to-cloud access to Amazon Athena data to create visualizations, reports, and more. This article provides step-by-step instructions on connecting to Amazon Athena within Connect Cloud and creating visualizations using Amazon Athena data in Klipfolio.
CData Connect Cloud offers a direct cloud-to-cloud interface for Amazon Athena, enabling you to construct reports from real-time Amazon Athena data data within Klipfolio—without the need for data replication to a database natively supported by Klipfolio. While building visualizations, Klipfolio generates SQL queries to fetch data. With optimized data processing capabilities out of the box, CData Connect Cloud efficiently directs all supported SQL operations (such as filters, JOINs, etc.) directly to Amazon Athena, harnessing server-side processing to swiftly retrieve the requested Amazon Athena data data.
Configure Amazon Athena Connectivity for Klipfolio
Connectivity to Amazon Athena from Klipfolio is made possible through CData Connect Cloud. To work with Amazon Athena data from Klipfolio, we start by creating and configuring a Amazon Athena connection.
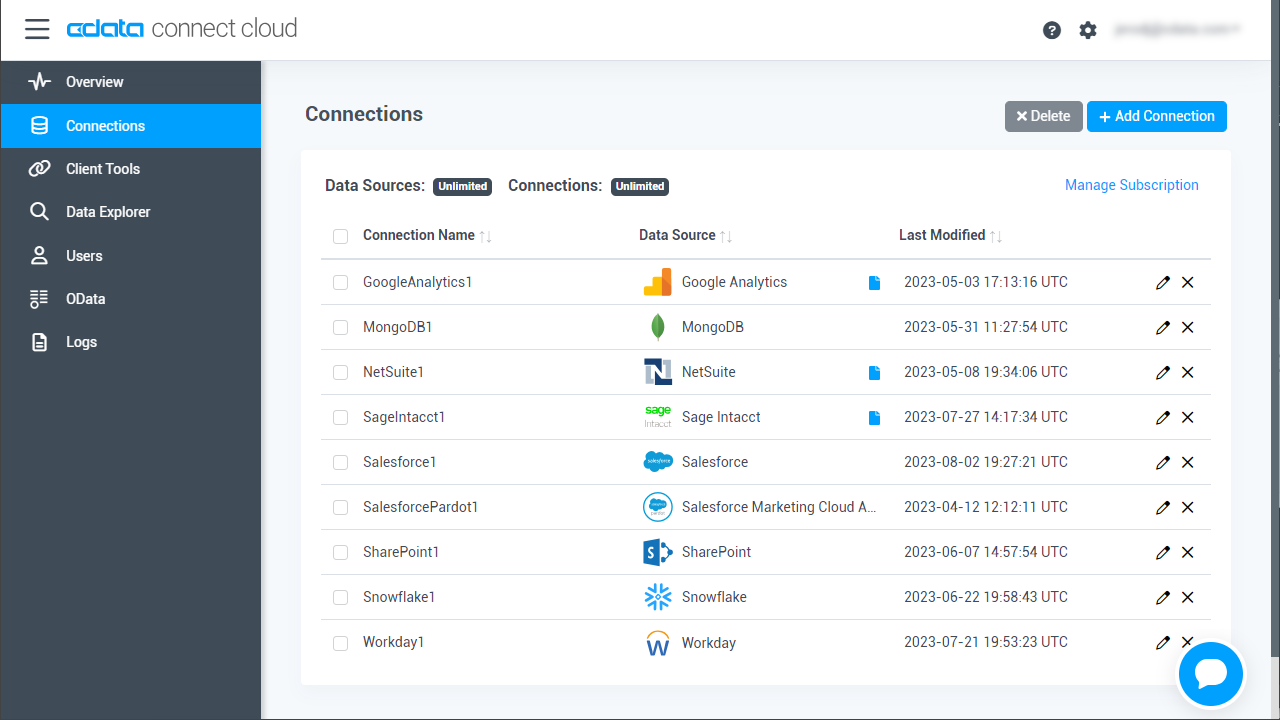
- Log into Connect Cloud, click Connections and click Add Connection
![Adding a Connection]()
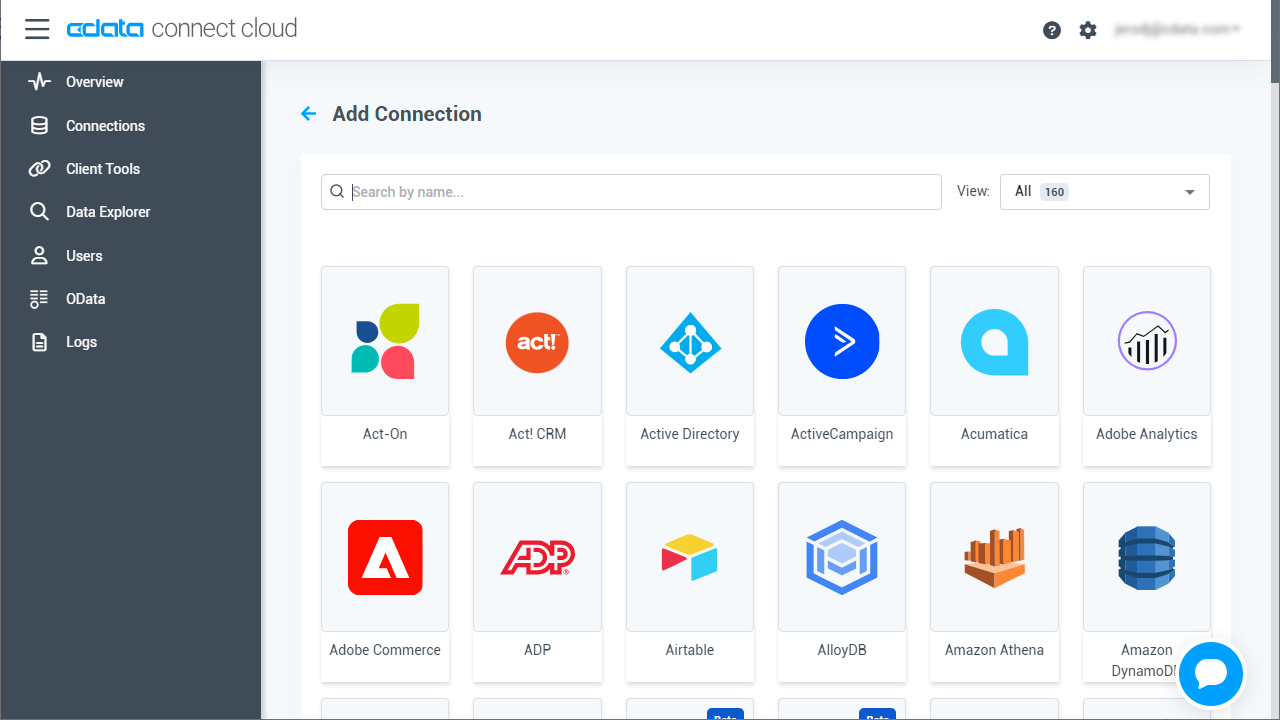
- Select "Amazon Athena" from the Add Connection panel
![Selecting a data source]()
-
Enter the necessary authentication properties to connect to Amazon Athena.
Authenticating to Amazon Athena
To authorize Amazon Athena requests, provide the credentials for an administrator account or for an IAM user with custom permissions: Set AccessKey to the access key Id. Set SecretKey to the secret access key.
Note: Though you can connect as the AWS account administrator, it is recommended to use IAM user credentials to access AWS services.
Obtaining the Access Key
To obtain the credentials for an IAM user, follow the steps below:
- Sign into the IAM console.
- In the navigation pane, select Users.
- To create or manage the access keys for a user, select the user and then select the Security Credentials tab.
To obtain the credentials for your AWS root account, follow the steps below:
- Sign into the AWS Management console with the credentials for your root account.
- Select your account name or number and select My Security Credentials in the menu that is displayed.
- Click Continue to Security Credentials and expand the Access Keys section to manage or create root account access keys.
Authenticating from an EC2 Instance
If you are using the CData Data Provider for Amazon Athena 2018 from an EC2 Instance and have an IAM Role assigned to the instance, you can use the IAM Role to authenticate. To do so, set UseEC2Roles to true and leave AccessKey and SecretKey empty. The CData Data Provider for Amazon Athena 2018 will automatically obtain your IAM Role credentials and authenticate with them.
Authenticating as an AWS Role
In many situations it may be preferable to use an IAM role for authentication instead of the direct security credentials of an AWS root user. An AWS role may be used instead by specifying the RoleARN. This will cause the CData Data Provider for Amazon Athena 2018 to attempt to retrieve credentials for the specified role. If you are connecting to AWS (instead of already being connected such as on an EC2 instance), you must additionally specify the AccessKey and SecretKey of an IAM user to assume the role for. Roles may not be used when specifying the AccessKey and SecretKey of an AWS root user.
Authenticating with MFA
For users and roles that require Multi-factor Authentication, specify the MFASerialNumber and MFAToken connection properties. This will cause the CData Data Provider for Amazon Athena 2018 to submit the MFA credentials in a request to retrieve temporary authentication credentials. Note that the duration of the temporary credentials may be controlled via the TemporaryTokenDuration (default 3600 seconds).
Connecting to Amazon Athena
In addition to the AccessKey and SecretKey properties, specify Database, S3StagingDirectory and Region. Set Region to the region where your Amazon Athena data is hosted. Set S3StagingDirectory to a folder in S3 where you would like to store the results of queries.
If Database is not set in the connection, the data provider connects to the default database set in Amazon Athena.
![Configuring a connection (Salesforce is shown)]()
- Click Create & Test
- Navigate to the Permissions tab in the Add Amazon Athena Connection page and update the User-based permissions.
![Updating permissions]()
Add a Personal Access Token
If you are connecting from a service, application, platform, or framework that does not support OAuth authentication, you can create a Personal Access Token (PAT) to use for authentication. Best practices would dictate that you create a separate PAT for each service, to maintain granularity of access.
- Click on your username at the top right of the Connect Cloud app and click User Profile.
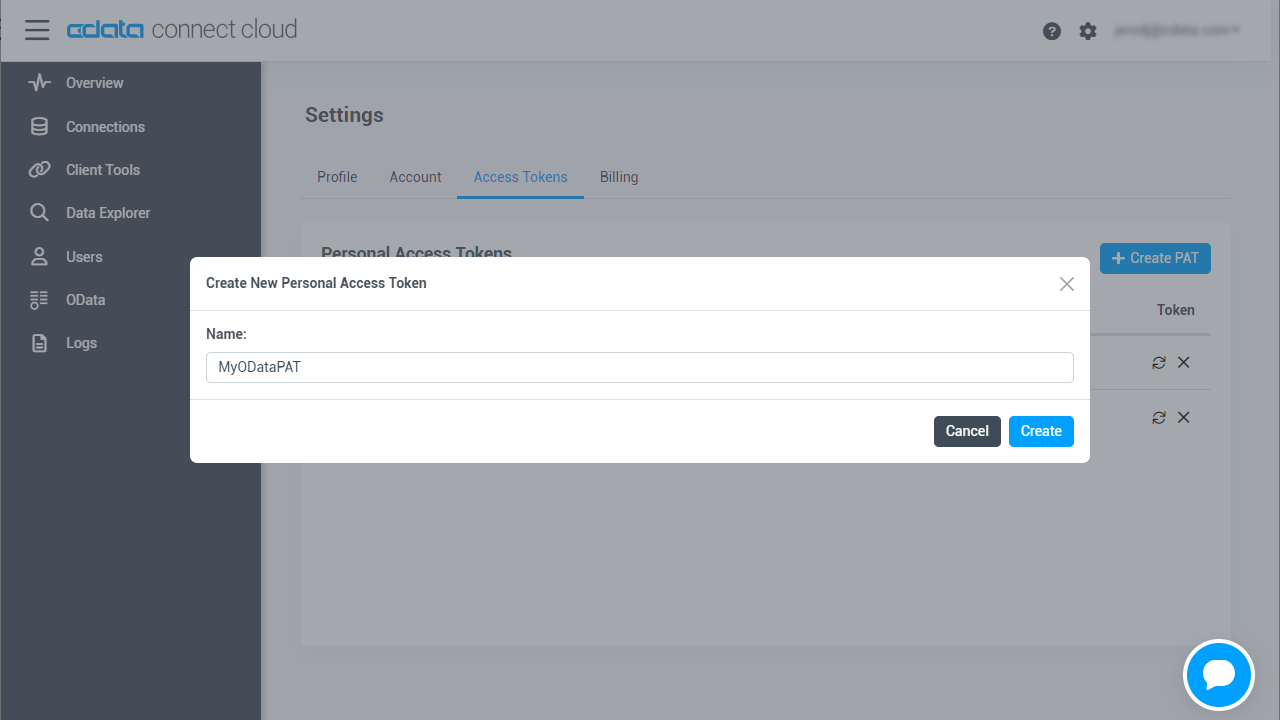
- On the User Profile page, scroll down to the Personal Access Tokens section and click Create PAT.
- Give your PAT a name and click Create.
![Creating a new PAT]()
- The personal access token is only visible at creation, so be sure to copy it and store it securely for future use.
With the connection configured, you are ready to connect to Amazon Athena data Klipfolio.
Connect to Amazon Athena from Klipfolio
The steps below outline connecting to CData Connect Cloud from Klipfolio to create a new Amazon Athena data source.
- Open Klipfolio
- Click in Data Sources to add a new data source
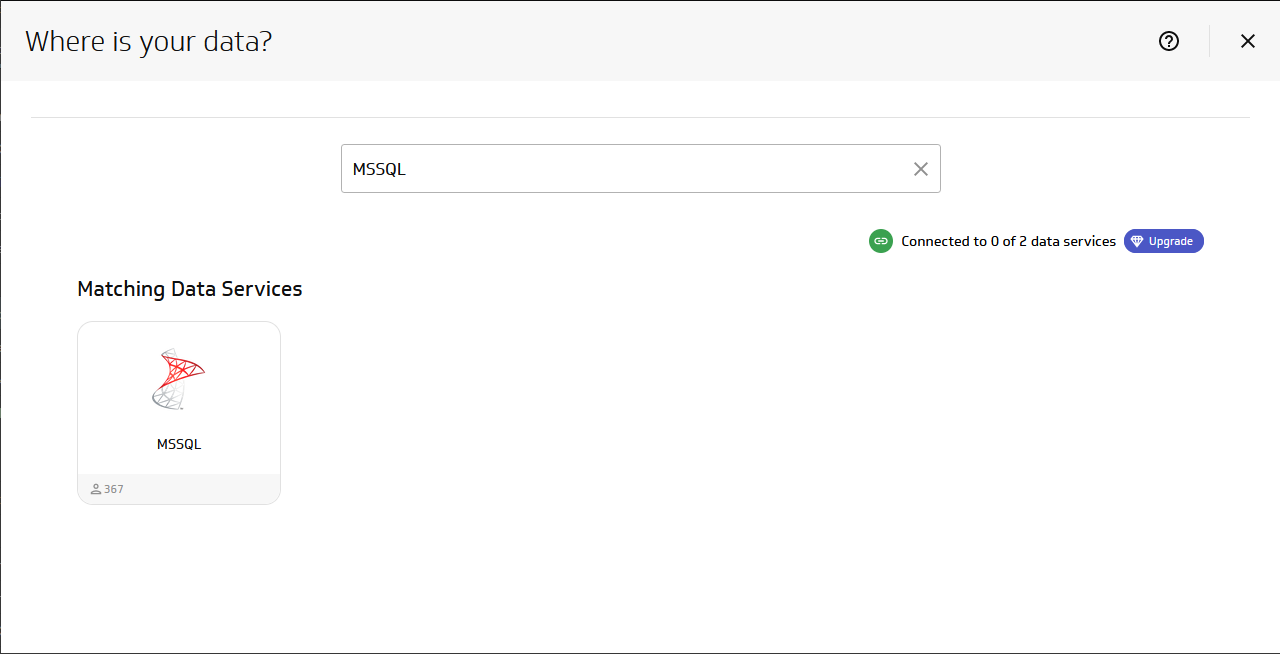
- Search for and select MSSQL as the Service
![Adding a new datasource.]()
- Click "Create a custom MSSQL data source"
- Configure the data source by setting the MSSQL connection properties:
- Host: tds.cdata.com
- Port: 14333
- Database: your database (e.g., AmazonAthena1)
- Driver: MS SQL
- Username: a Connect Cloud user (e.g. user@mydomain.com)
- Password: the above user's PAT
- SQL Query: any query to retrieve data (e.g. SELECT * FROM Customers )
- Select the checkbox to "Include column headers"
- Select the checkbox to "Use SSL/TLS"
![Configuring the connection to Connect Cloud.]()
- Click "Get data" to preview the Amazon Athena data before building a data model.
Build a Data Model
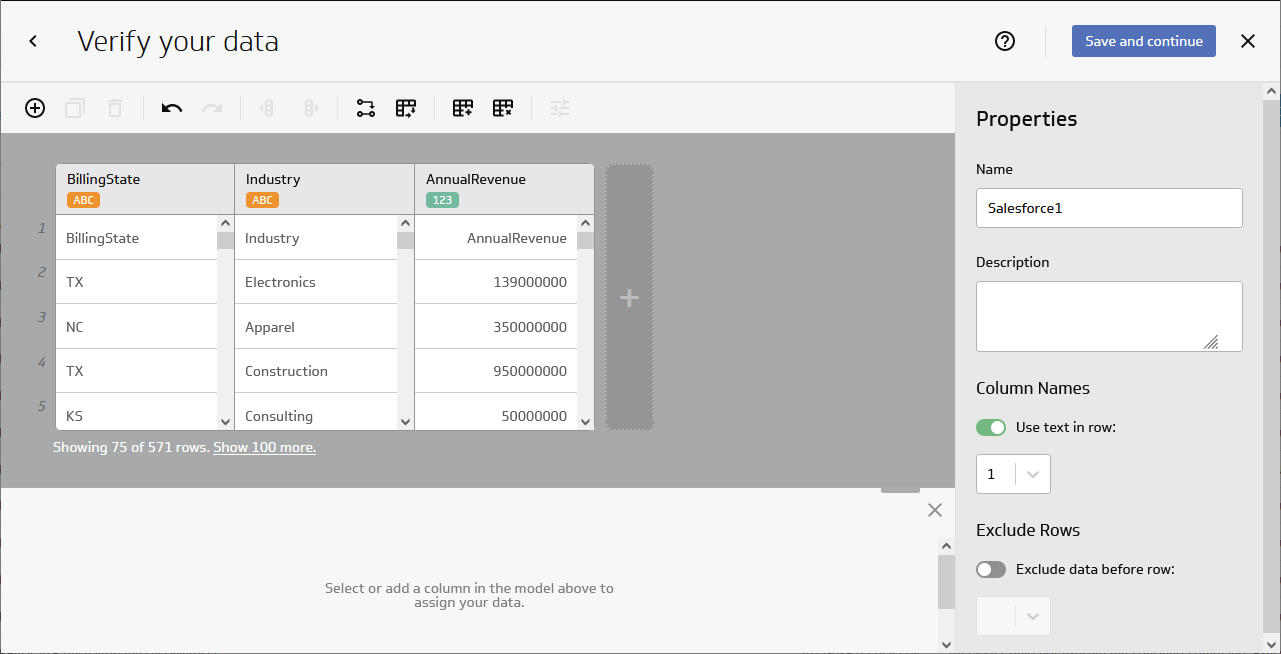
After retrieving the data, click the checkbox to "Model your data" and click "Continue." In the new window, configure your data model.
- Confirm that the model includes all columns you wish to work with
- Name your model
- (optional) Set the Description
- Set "Header in row" to 1
- Click the toggle to "Exclude data before row" and set the value to 2
- Click "Save and Exit"
![Configuring the data model.]()
Create a Metric
With the data modeled, we are ready to create a Metric (or visualization) of the data to be used in the Klipfolio platform for dashboards, reporting, and more.
- Click "Create metrics"
- Select a Data source
- Select a Metric value and default aggregation
- Select Segmentation(s)
- Select a Date & time
- Select a Data shape
- Configure the Display settings
- Click Save
![Configuring a Metric]()
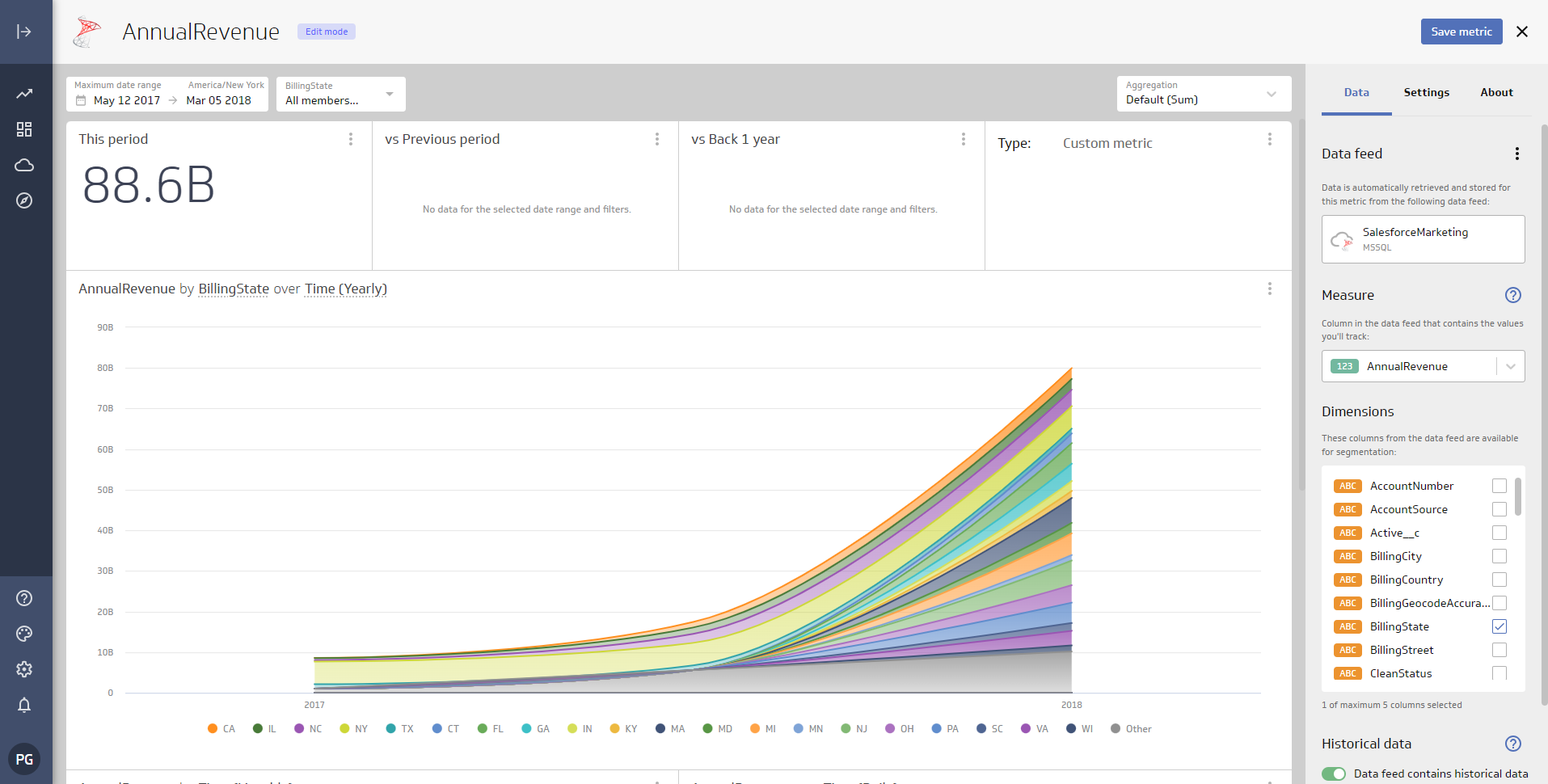
- Navigate to your Metric and further configure the visualization
![A configured Metric]()
SQL Access to Amazon Athena Data from Cloud Applications
Now you have a Metric built from live Amazon Athena data. You can add it to a new dashboard, share, and more. Easily create more data sources and new visualizations, produce reports, and more — all without replicating Amazon Athena data.
To get SQL data access to 100+ SaaS, Big Data, and NoSQL sources directly from your cloud applications, try CData Connect Cloud.